IT Security Audit Log Software
Accountability is vital to the success of any business. Audit logs keep everyone on the same page, and ensure nothing falls through the cracks—no more wondering who made a change, when and where.
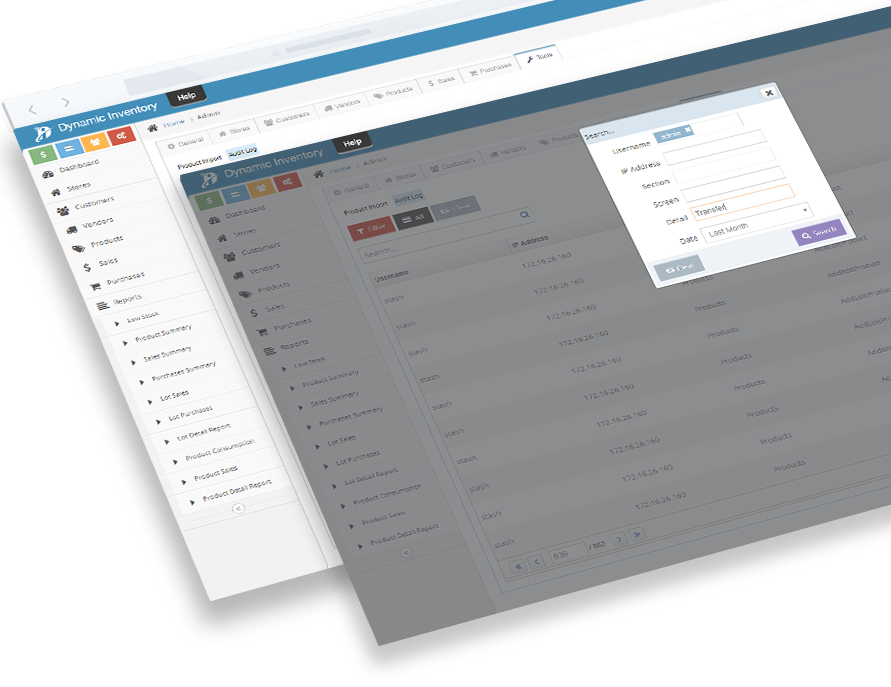
Accountability is vital to the success of any business. Audit logs keep everyone on the same page, and ensure nothing falls through the cracks—no more wondering who made a change, when and where. Depending on how strict your IT department is, you may or may not have access to the audit logs within the different systems you use. Taking a Big Brother approach to audit logging can help to catch sneaky team members that might be lying about the actions they have performed to complete their job duties. It’s important to capture viewing of screens, editing, and deleting with this approach. When an audit is performed in Dynamic Inventory you are able to see all these details, and restrict the list of logs down to individual users. Additionally, the IP Address is logged for every action including login attempts to aid in information security audits. Audit logging can also be used to promote transparency within an organization. In Dynamic Inventory, your administrator can enable audit logging for your user account. The login activity, including the last login date/time of all users, is visible to all users on the dashboard. With Dynamic Inventory there is a trail that can be tracked from beginning to end.
What Is An Audit Log?
An audit log within inventory software is a comprehensive list of different functions that were used by users within a specific time period. Some audit logs are more detailed than others. All audit logs should be composed of a verified user, action performed, and date at the very least.
Verified User
The username alone is not enough to identify the actual person who logged in if someone shares the password. In Dynamic Inventory, we use a combination of IP address and username to identify the verified user.
Action Performed
This is the physical click that results in some type of action within the software. Common actions performed include viewing, adding, editing, and deleting.
Date
You can reference the date an action was performed by a verified user. Dynamic Inventory allows you to sort/filter by audit log dates.
Features To Improve Record Keeping
Gain valuable insights from your data with features that automate inventory processes.
Benefits of Dynamic Inventory’s Low Stock Alert System:
Dynamic Inventory barcode scanning software is a must-have for modern inventory management operations, and here are the reasons why:
Audit Records Going Back To Day One
Track activity going as far back as needed. Since users with history cannot be deleted, but only deactivated, never worry about losing records as your workforce changes. Your history will stay intact no matter what administrative changes occur.
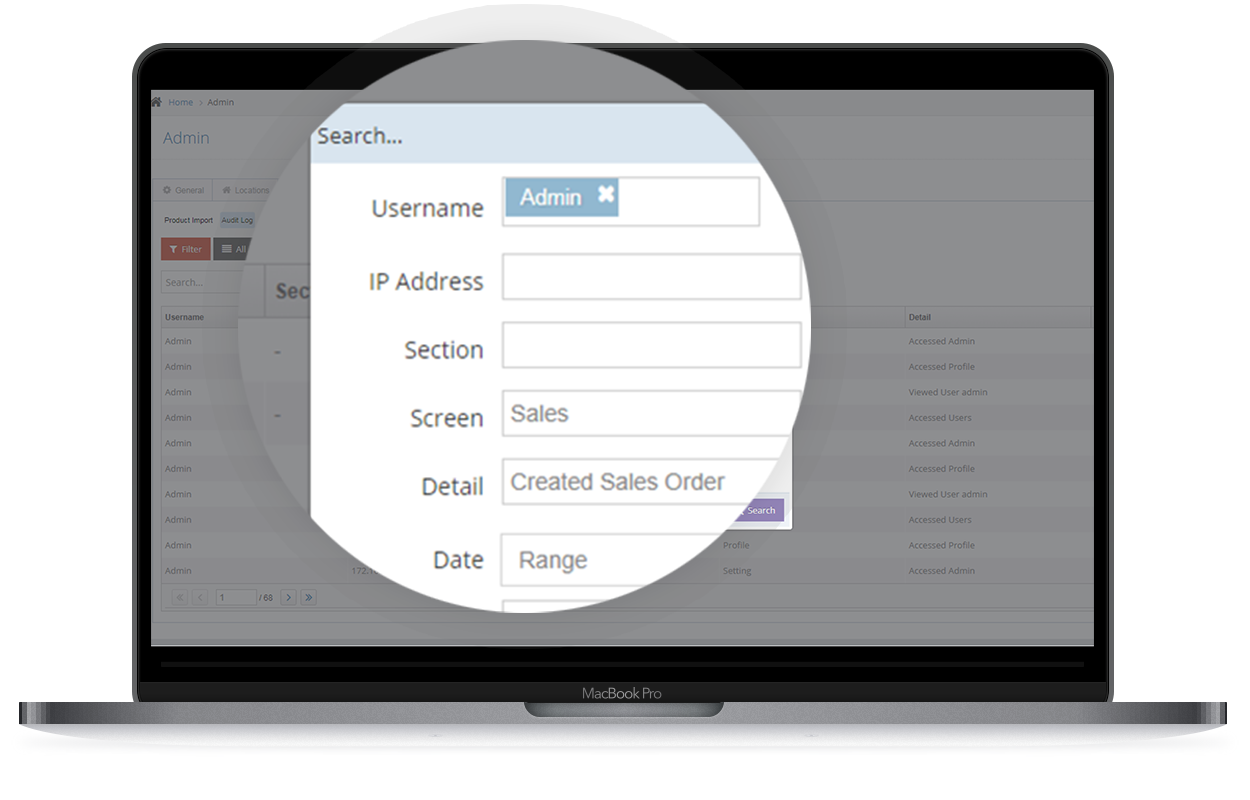
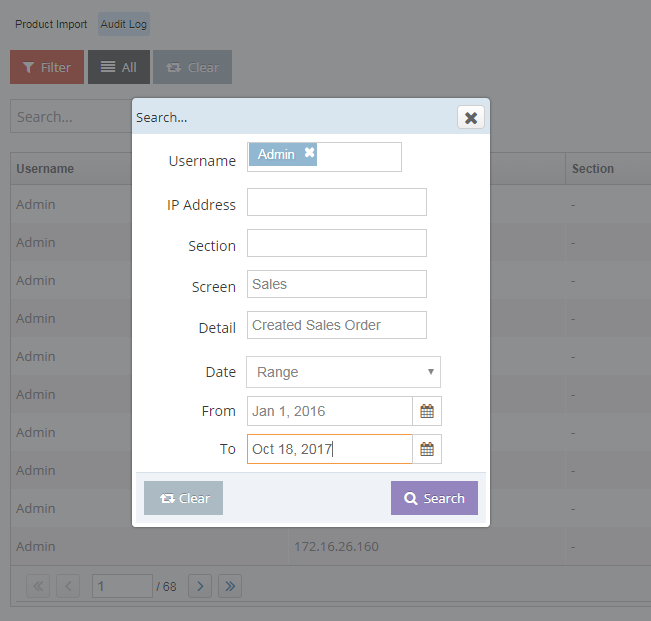
Detailed Filters and Search
Search by username, IP address, screen, action taken and even by date. With Dynamic Inventory’s audit log, you will always have the who, what, when and why.
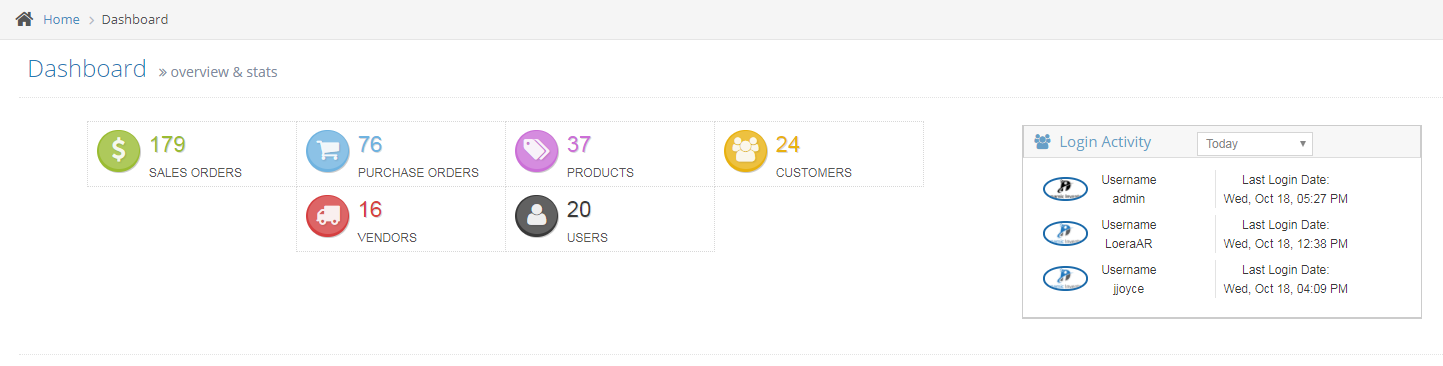
Login Activity Visible On Dashboard
You can view a dedicated section on the dashboard that provides the last login activity for each user. Additionally, you can see which users logged in last week vs. this week and make sure team members are consistently accessing the system.
Learn how Dynamic Inventory can streamline your business today!
What Audit Logging Tools Does Dynamic Inventory Use?
There are several tools we use internally to track the day-to-day operations of developing software. Many of the audit log features in Dynamic Inventory are inspired by the auditing logging tools we are familiar with. If you choose to host your system through our hosting partner, we will monitor the server for problems remotely using a tool called Nagios. Nagios sends keeps a detailed record of all services running, and any technical errors that may arise due to memory fluctuations and peak processing on the server. As you grow with Dynamic Inventory, we are able to tell you how healthy your server setup is for the number of users you need based on the audit logging and monitoring policies within Nagios. Another audit tool we run continuously against your installation is Uptime Robot. If there are any DNS fluctuations or a DDOS attack against your system causing the URL not to resolve we are immediately notified by Uptime Robot. We use JIRA internally for managing user stories and feature requests. We are able to see which clients requested what features, and can give you real-time updates on any soon-to-be-released functionality. This is all possible based on the comments logged against the story in JIRA. Finally, we use Freshdesk to manage all support tickets and it keeps a detailed log of all conversations and communication between clients and our customer support heros on the ticket. We are firm believers that great software starts with keeping thorough logs.
Audit Log Software Features in Dynamic Inventory
Stay on top of user activity, and never wonder who did what again.



